AI for Communications
AI for communications is a major research direction of our group. In addition to projects listed in this page, please also follow links below to other related work:
- Dr. Tianhua Xu https://warwick.ac.uk/fac/sci/eng/research/grouplist/connectedsystems/comsys/optical_comms_sensing/
- Prof. Gan Zheng https://warwick.ac.uk/fac/sci/eng/research/grouplist/connectedsystems/comsys/wireless/
- Dr Adam Noel https://warwick.ac.uk/fac/sci/eng/research/grouplist/connectedsystems/comsys/molcomms-new/
- Dr Subhash Lakshminarayana https://warwick.ac.uk/fac/sci/eng/research/grouplist/connectedsystems/comsys/cps_security/
1. Detection of Pepper Yellow Leaf Curl Virus in Chilli Plants
Phd: Dyah Agustika (Supervisors: Dr Mark Leeson, jointly supervised with Daciana).

Leaves from a PYLCV-infected tree |

Leaves from a healthy tree |
Chilli is a superior commodity produced and cultivated by most Indonesian farmers but it us attacked by the Pepper Yellow Leaf Curl Virus (PYLCV). This virus can cause abnormal development of the plants and the inhibition of fruit formation. This project aims to find an early detection system for chilli plants infected by PYLCV based on the emission of Volatile Organic Compounds (VOCs) and changes in plant morphological expression. An electronic nose (e-nose) is used to detect VOCs emitted by healthy and infected plants, and a thermal camera and Fourier Transform Infrared (FTIR) spectroscopy are applied to detect plant morphological changes. The optimization of feature extraction and pattern recognition method is done to improve the performance of e-nose, thermal camera and FTIR spectroscopy. Preliminary work used Gas Chromatography-Mass Spectrometry (GC-MS) test and FTIR Spectroscopy to examine healthy and infected chilli plants. The GC-MS results showed that VOCs emitted by PYLCV-infected and PYLCV-free chilli plants could be distinguished. Furthermore, FTIR spectroscopy with the signal pre-processing has succeeded in discriminating between healthy and infected plants.
Selected publications
- K. Agustika, I. Mercuriani, C. W. Purnomo, S. Hartono, K. Triyana, D. D. Iliescu and M. S. Leeson, “Fourier transform infrared spectrum pre-processing technique selection for detecting PYLCV-infected chilli plants”, Spectrochimica Acta Part A: Molecular and Biomolecular Spectroscopy, vol. 278, art. 121339 [12 pages], 2022.
- K. Agustika, I. S. Mercuriani, N. A. Ariyati, C. W. Purnomo, K. Triyana, D. D. Iliescu and M. S. Leeson, “Gas Chromatography-Mass Spectrometry Analysis of Compounds Emitted by Pepper Yellow Leaf Curl Virus (PYLCV)-infected Chilli Plants: A Preliminary Study”, Separations, vol. 8, no. 9, art. 136 [14 pages], 2021.
Conference publications to date:
- K. Agustika, S. H. Hidayat, M. R. Nawawi, D. D. Iliescu and M. S. Leeson, “Savitzky-Golay Parameter Optimization by using Linear Discriminant Analysis for FTIR Spectra”, 7th IEEE Forum on Research and Technologies for Society and Industry (RTSI 2022), Paris, France, 24-26 August 2022 (TRACK 3.1, Thursday, August 25 14:30 – 15:00).
- K. Agustika, N. A. Ariyanti, I. N. K. Wardana, D. D. Iliescu and M. S. Leeson, “'Classification of Chili Plant Origin by Using Multilayer Perceptron Neural Network”, 8th International Conference on Electrical Engineering, Computer Science and Informatics (EECSI), Semarang, Indonesia, October 20-21, 2021, pp. 365-369.
- D. K. Agustika, S. N. Hidayat, K. Triyana, D. D. Iliescu and M. S. Leeson, “Feature extraction optimization on steady-state response to enhance electronic nose performance”, 7th International Conference on Electrical Engineering, Comput
2. Machine Learning for Network Traffic Generation and Classification
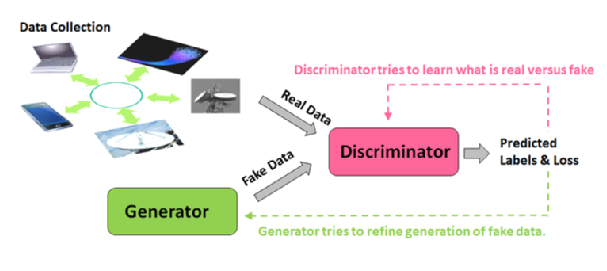
GAN operation |
|
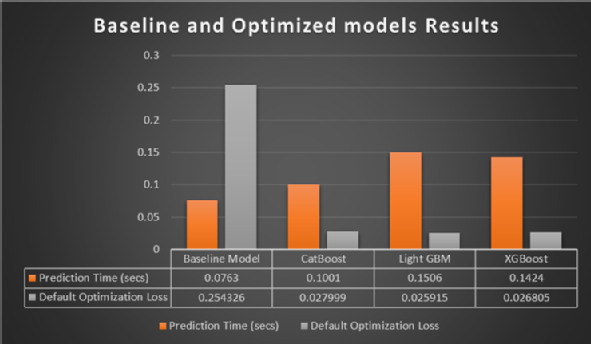
Boosting method results |
PhD: Tertseghe Joseph Anande (Supervisors: Dr Mark Leeson)
Recent trends in networks and cyber systems have continued to expose security vulnerabilities due to the large volume of data transmission and the associated complexities in the systems. With increased infiltrations caused by adversarial attacks on these network systems and infrastructure, critical sectors as energy, finance, healthcare, telecoms, aerospace, education, chemical, hi-tech, oil and gas, and governments have continued to experience diverse and varying degrees of intrusions instigated by sophisticated attack methods that are able to evade existing security systems. This project is investigating these attack patterns, then designing and developing generative and hybrid Machine Learning methods for network traffic data synthesis and meta classification of multiple attack patterns in real and synthetic data distributions. Deep Learning algorithms based on different Generative Adversarial Network (GAN) architectures have been utilized to generate synthetic data samples with highly similar distribution patterns as the original data samples. Synthetic data generation has been achieved without sight of the real data and using noise as input data. The study is further investigating optimization of state-of-the-art Ensemble Learning (EL) algorithms for constructing Meta Learning frameworks and implementation for enhanced multi-attack analysis of synthetic and real network traffic data.
Publications to date:
- J. Anande, S. Al-Saadi and M. S. Leeson, “Generative Adversarial Networks for Network Traffic Feature Generation”, International Journal of Computers and Applications, in press.
- J. Anande and M. S. Leeson, “Generative Adversarial Networks (GANs): A Survey of Network Traffic Generation”, International Journal of Machine Learning and Computing, vol. 12, no. 6, pp. 333-343, 2022.
3. Network Intrusion Detection for Software-Defined Networking using Deep Learning
Ph D: Sami Al-Saadi (Supervisors: Dr Mark Leeson)
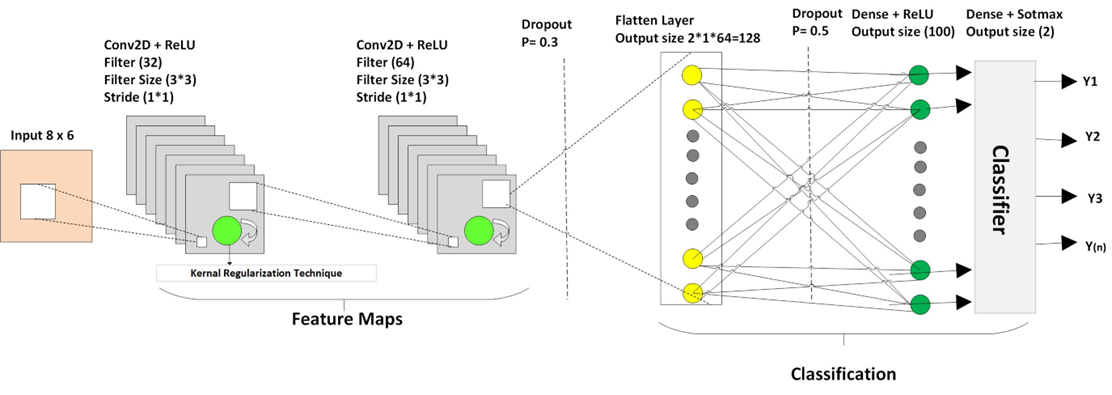
Typical convolutional neural network Architecture
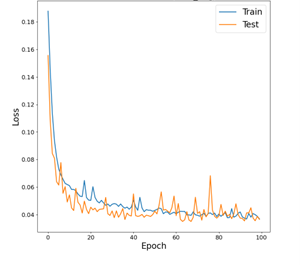
Typical loss using new regularisation method
Software-Defined Networking (SDN) architectures decouple network control and data forwarding functions, enabling network control to be directly programmable and the underlying infrastructure to be abstracted from applications. SDN is a promising networking platform that changes the current network architectures and services. While the networking community has focused on SDN, the security community has been relatively slow in embracing SDN technology. However, the intelligent centralization has its own drawbacks when it comes to security, scalability, and elasticity. The consideration of SDN network security functions remains in the early stages, with few existing case studies. SDN networks possess a controller that manages flow control to the switches or routers and the deployment of applications. This work aims to implement a Network Intrusion Detection System (NIDS) with deep learning (DL) within the SDN Controller to detect early attacks on the network. Current work uses convolutional neural networks and the application of new regularisation methods, which help the models to generalise and aid performance on unseen data.
