Student Blog Collection
My Job Success Story: Can be your success story too! (Part Four)
As promised in my previous blog post (My Job Success Story: Can be your success story too! (Part Three)Link opens in a new window), here is the continuation of the success story to secure my job.
At the end of the interview, the interviewer would open the floor to ask questions. GRAB THIS OPPORTUNITY! You are marked the most on these questions. These last 10-15 minutes helps the interviewer to understand how eager and excited you are to know about their company.
I cannot stress enough to stay in touch with your recruiter (the person who contacted you on day one). (S)He is your best friend throughout this recruitment journey. (S)He will advise and guide you and try everything possible to help you get the job if you are the right fit for the role. Always keep them posted via email or telephone after your interview and any change in circumstances.
Finally, in November 2021, the day arrived when I received my first offer. Please do not get excited and listen to all the salary benefits carefully on the call. Always maintain written agreement. Eventually, the recruiter will proceed ahead with your official contract. Please do not stop attending interviews until you sign the official contract. In case, you have received multiple offers, try and negotiate with the second and third companies. My advice is: Do not burn bridges with your first company with whom you have signed the official first contract. But again, it is not set in stone you can follow what suits you the best.
To summarise, this is my success story. I hope you can pick up and learn a few things and make it your success story too!!!
My Job Success Story: Can be your success story too! (Part Three)
As promised in my previous blog post (My Job Success Story: Can be your success story too! (Part Two)Link opens in a new window), here is the continuation of the success story to secure my job.
I will be generous and share my secret to prepare for these interviews.
Recruiter-round interview –
- Ensure you prepare your life journey in a story-telling format with positive impacts on the Clients and their business
- Begin your strengths by saying - "My previous Manager Mr Thomas Sheckle mentioned in my feedback that I hone ABC quality...". As this helps the interviewer that not only you think this is your strength but also your supervisor or higher management echo it
- Please prepare for at least three weaknesses and do not answer saying there is no weakness I can recollect, or I am Pitch Perfect!
- Read and understand the job description carefully. Express how your work experience can cause a positive impact on the company and its associated clients.
- Read the latest annual report of the company. Capture two-three company's facts/elements that are not readily available on the internet website. The interviewers appreciated that I did my homework about the company.
- Always read and understand the company's value and be prepared to justify your favourite one.
Technical interview –
- I used to search my interviewers on LinkedIn and try and find some common aspects to talk about during the first 5 minutes of the interview. It will help you in breaking the ice!
- The only tip is to be well versed with your CV and remember your top five to six skillsets with some stories to share.
Competency interview –
- I had framed twenty-five stories based on my work and educational experience in a STAR format. Yes, you have read the number correctly!
- Later, I hashtagged each of the stories. For instance, #Conflict or #ProudMoment. It was easy to remember and acted as a catalyst in correlating with the question.
- After each interview, you note down which story you have used and cross over to that story for the next round of interviews in the same company. Please ensure you do not repeat the stories in the following interview rounds.
Please read my next blog (My Job Success Story: Can be your success story too! (Part Four)Link opens in a new window) to weave in your success story from my learnings and experience.
My Job Success Story: Can be your success story too! (Part Two)
As promised in my previous blog post (My Job Success Story: Can be your success story too! (Part One)Link opens in a new window), here is the continuation of the success story to secure my job.
To kick start the job search, I started shortlisting the list of companies. In essence, the companies should get finalised by the end of April 2021. Fortunately, my CV was ready and up-to-date with all my recent achievements. So, I started applying left, right and centre to numerous shortlisted companies. For five consecutive days, I diligently applied for jobs with minimal breaks. As I knew, I was running far behind in the process. My advice is: please do not compare yourself with others if you are ahead or lagging in the job-securing process.
After applying to thirty different companies, the waiting game was on where my patience got tested. The trick is - One does not sit ideal as the other two activities are still pending. Firstly, applying to other companies as per the suggestion from renowned portals like LinkedIn, job search, indeed, and many others. Secondly, the significant and game-changing step in the process is to prepare yourself for the interview.
You need to prepare yourself for three different types of interview questions: recruiter-round, technical and competency interview. I have listed commonly asked questions based on my personal experience.
Recruiter-round interview –
- Why XYZ Company?
- Tell me about your strengths and weakness?
- What is your motivation?
- What are you looking for?
- Why are you the best fit for this role?
Technical interview –
- There are no set questions for this round as the interviewer goes through your CV and asks questions related to your work experience.
Competency interview –
- Tell us about your achievement that you are proud of?
- Tell us about a time you got into a conflict and how did you resolve it?
- Tell us about a time when you overcame an obstruction?
- Have you ever handled a difficult client? If yes, then how did you handle the situation (Please do not answer that you have not experienced this as we all have had some experience)
- What is your perspective about leadership and what sort of leader are you?
- How do you announce bad news to your fellow team members?
- Tell us a time when the Client team did not agree with your idea, and you still went overboard and convinced the Client team?
Please read my next blog (My Job Success Story: Can be your success story too! (Part Three)Link opens in a new window) to weave in your success story from my learnings and experience.
My Job Success Story: Can be your success story too! (Part One)
The day I entered the University, students, staff and professors started talking about securing a job. To my dismay, I did not sign up for a job opportunity before even I secure my master’s degree. Back home (India), the job placement process is different to what we have in place in the UK. In the UK, one needs to hunt and hone a job opportunity on their own without any assistance from the University or placement officer. But the University of Warwick does aid the students in their careers and jobs in terms of - creating a CV, cover letter, preparing for interviews and psychometric assessment, and many other careers advice.
During my first week, I got back home with a big question in my mind – Do I apply for a graduate scheme or experienced hire? For those who do not know my background, before doing my master’s degree I had nine years of work (IT) experience with Accenture. I received the advice to pursue a graduate scheme job (keep it in my back pocket), and the coming months go for experienced hire. On further discussion with my network and attending cyber security career fairs, mid-December 2020, I decided to follow the path of experience hire. My career decision may not stand true for everyone as each individual have different career growth.
Fast-forwarding to May 2021. According to the plan on paper, I should have started my job-hunting process by applying to multiple organisations. Due to the aftermath of the Covid-19 pandemic, I failed to adhere to the plan. Hence, I decided to push it further to July 2021. Again, my job application slipped as I was lagging in my project work. At last, I progressed with my job applications at the end of September 2021, once I submitted my project. Please do not delay your job application and repeat the same mistake as I did. Try and stick to your timelines and deadlines.
Please read my next blog (My Job Success Story: Can be your success story too! (Part Two)Link opens in a new window) to weave in your success story from my learnings and experience.
Is learning experience directly proportional to teaching quality?
I am a firm believer of teaching holds the scope of learning in itself. The one who teaches learn at the same time and it is supported by Robert Heinlein famous quote: “When one teaches, two learn”. The student’s learning experience is contributed majorly by the teaching quality. You must have heard that the University of Warwick has been named the University of the Year for Teaching Quality and as runner-up for University of the Year by the Sunday Times Good University Guide 2022. Further reading is available on the following website.
I would like to share my learning experience and we get to eventually deduce the teaching quality of the University of Warwick.
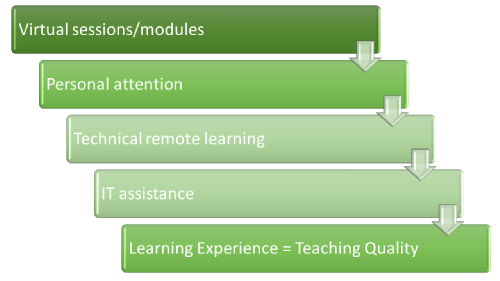
Virtual sessions/modules:
All the modules except for the last one was virtually scheduled. But it always felt so close to the real world. The preparation and planning for these sessions were commendable. The timetable was shared with the students so that we could plan our week accordingly. With the use of the Microsoft (MS) Team, all the students collaborated on their ideas during case studies and other group activities. Kudos to the university for choosing MS Team and providing sessions on how to use MS Teams.
Personal attention:
Alike pre-covid, the personal tutors still met their mentees on MS Teams call (virtually). But the attention and guidance provided by them remained intact. Moreover, discussing the PMA feedback one on one sessions with the module leader was an easy option during this tough time of Covid-19.
Technical remote learning:
Modules involving technical labs were crafted bearing in mind remote learning. Never did I get this feeling of being lost as the module leader would resolve the issue with the help of screen share. Technology has genuinely bridged the gap between humans sitting miles apart. But the patience and effort of the teaching staff of WMG should be appreciated.
IT assistance:
During the work from home modus operandi, IT assistance was always provided by just calling the university’s IT service desk. I was stuck about three-four times and each time my ticket was resolved within a couple of hours. All this put together, helped me achieve my PMA deadline.
My simple mantra in life is by Aristotle: “Those who know, do. Those that understand, teach.”. I am sure, after this blog post you, all would understand the teaching standards and quality delivered by WMG, University of Warwick!
Tips and Tricks to achieve distinction…
When at the University of Warwick, you might hear the following statement often: “A poorly worded report will hide excellent content”. Personally, time and again, I heard the above statement from my supervisor and personal tutor. Module after module, I started abiding by this statement which helped me gain distinction. Here are a few tips and tricks to secure distinction in your PMA’s and Dissertation. I hope this works out for you, and you can walk out of the University of Warwick with a Distinction!
- Ensure that your PMA/Dissertation has a front-page comprising a title, your student number, module and lecturer’s name.
- Imbibe the practice of including an executive summary giving a gest of the entire PMA/Dissertation.
- The table of contents and list of figures and tables should display correct page numbers and hyperlink correctly.
- An introduction section acts as a map to the rest of the document. I categorised the introduction into three sub-sections: Purpose of the document (including in-scope and out-of-scope), Target audience, and Document structure.
- A logical and well-defined document structure with headings and subheadings.
- Clearly labelled and well-presented diagrams and other graphics are discussed in the text. Always recreate or adapt the diagrams from your reference and do not copy-paste the exact figure. I used to create figures with the help of smart art in Microsoft PowerPoint Presentation and save them as an image.
- Evidence of systematic and clear thinking, indicative of good planning and organisation. A critical style of writing which compares and contrasts the main theories, concepts and arguments with conclusions that are based on the evidence presented.
- Include a Conclusion section at the end to summarise your discussion and preventive measures or mitigation actions.
- Write a short sentence that is not more than twenty words.
- Your document should be proofread, and grammar checked. Ensure that you follow British English spellings.
- Reference should be Harvard or the one required by your department. Referencing and citation accuracy is the key to good documentation.
- Adhere to the document submission timeline, word count and the number of pages (only if mentioned in the PMA question). Also, follow the PMA question and do not include Appendix if explicitly stated.
- Read the PMA question carefully and submit the document in the expected format. Sometimes, you need to submit more than one document and understand the requirement of the other documents, for instance, format/type.

Overview of Cyber Security and Management Modules – Part Two
As promised in my last blog post (Overview of Cyber Security and Management Modules – Part One), here is the continuation of the modules overview as part of the Cyber Security and Management MSc course.
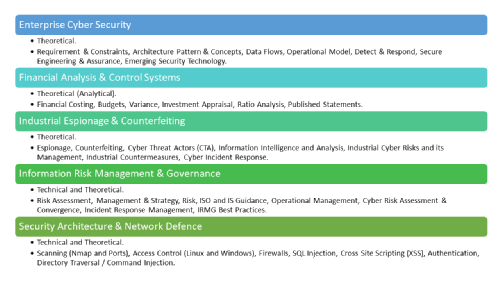
5. Enterprise Cyber Security
Module type: Theoretical.
Topics and concepts covered: System Context, Requirement and Constraints, Architecture Concepts, Component and Data Flows, Operational Model, Architecture Pattern, Detect and Respond, Secure Engineering and Assurance, Emerging Security Technology.
Learning outcomes: Persuasively articulate cyber security imperatives to key decision-makers in an organisation. Critically evaluate the cyber security posture of an organisation. Critically analyse “identity” in the context of the cyber security of an organisation's mission, considering both those inside and those outside the organisation. Critically analyse the cyber security consequences of the increasing connectedness of endpoint devices and control systems (such as sensors, actuators, buildings, and transportation) to an organisation's mission.
6. Financial Analysis & Control Systems
Module Type: Theoretical (Analytical).
Topics and concepts covered: Financial Costing, Budgets, Variance, Investment Appraisal, Ratio Analysis, Published Statements.
Learning outcomes: Interpret the basic business accounting statements. Differentiate between the different methods of measuring financial performance within a business. Critically analyse financial data to generate further information. Provide a critical interpretation of the relationship between the operational performance of a business and the financial measures of the business.
7. Industrial Espionage & Counterfeiting
Module type: Theoretical.
Topics and concepts covered: Espionage, Counterfeiting, Cyber Threat Actors (CTA), Information Intelligence and Analysis, Industrial Cyber Risks and its Management, Industrial Countermeasures, Cyber Incident Response.
Learning outcomes: Analyse exposure to industrial espionage. Synthesise appropriate mitigation to industrial espionage exposure. Critically analyse exposure in products and services to counterfeiting. Synthesise appropriate countermeasures to counterfeiting exposure in products and services.
8. Information Risk Management & Governance
Module type: Theoretical.
Topics and concepts covered: Information Risk Management, Risk Assessment, International Standards and Information Security Guidance, Risk Management Strategy, Operational Management, Cyber Risk Assessment, Incident Response Management, Cyber Risk Convergence, Risk Management and Governance Best Practices.
Learning outcomes: Compare and contrast various approaches to information risk management and select the most appropriate for a given scenario. Compare and contrast various approaches to information risk governance and select the most appropriate for a given scenario. Develop appropriate approaches to business continuity and resilience.
9. Security Architecture & Network Defence
Module type: Technical and Theoretical.
Topics and concepts covered: Scanning (Nmap and Ports), Access Control (Linux and Windows), Firewalls, SQL Injection, Cross-Site Scripting (XSS), Authentication, Directory Traversal / Command Injection.
Skillset gained: Burpe Suite, Kali Linux Virtual Machine, NMap, Netcat, Burp Suite, Gobuster, Google Authenticator, and online tools - Z85 Decoder and Encoder, HEX to ASCII code converter, ASCII to Hex code converter, and Crackstation.
Learning outcomes: Use terminology appropriately to describe current research in the cyber security domain. Analyse a network configuration (using tools as appropriate) to identify its security posture. Recommend suitable adjustments in the configuration of network security devices to achieve the desired security posture. Perform web penetration testing. Perform system penetration testing. Create firewall rules.
All the very best for your future CSM modules!
Overview of Cyber Security and Management Modules – Part One
As quoted by B.B. King, “The beautiful thing about learning is nobody can take it away from you”. I have gained and enhanced my knowledge, and no one can steal it away from me. However, I like to share my experience and learning outcomes of each of my modules. The best channel to share is by writing this blog post.
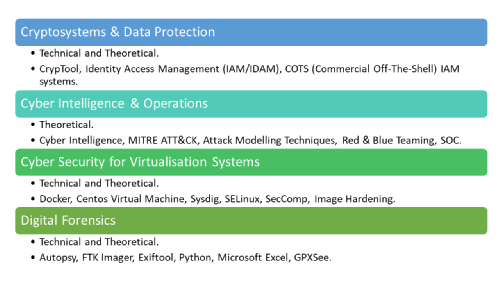
1. Cryptosystems & Data Protection
Module type: Technical and Theoretical.
Topics and concepts covered: Encryption, Hashing and Message Authentication Codes, Digital Signature, Digital Certificates, SSL, Kerberos, IPSEC.
Skillset gained: CrypTool, Identity Access Management (IAM/IDAM), COTS (Commercial Off-The-Shell) IAM systems.
Learning outcomes: Critically analyse the cryptographic needs of a particular scenario. Critically evaluate cryptographic solutions to an information assurance problem.
2. Cyber Intelligence & Operations
Module type: Theoretical.
Topics and concepts covered: Cyber Intelligence, MITRE ATT&CK, Attack Modelling Techniques, Red Teaming, Blue Teaming, Roles and Responsibilities of a SOC.
Learning outcomes: Reason about the threats and hazards to which a cyber system may be exposed with a view to producing actionable intelligence to reduce negative consequences. Evaluate the situational awareness of an organisation to the key indicators of its cyber well-being.
3. Cyber Security for Virtualisation Systems
Module type: Technical and Theoretical.
Topics and concepts covered: Cyber Virtualisation, Docker, Capabilities, Namespaces, Security Policy and Runtime Hardening – Security-Enhanced Linux (SELinux), Secure Computing (SecComp) and File System (Read-Only), Image Hardening, Registry and image distribution.
Skillset gained: Docker, Centos Virtual Machine, Sysdig, SELinux, SecComp, Image Hardening.
Learning outcomes: Analyse the security relationships within a virtualised ecosystem. Evaluate the extent to which a virtualised container ecosystem satisfies its desired security properties. Configure a virtualised container ecosystem to achieve the desired security properties from the perspective of both the container and the underlying host.
4. Digital Forensics
Module type: Technical and Theoretical.
Topics and concepts covered: Principles of Digital Forensics, Case Investigation, Management, Triage, and Forensics Acquisition, Examining and Reporting, File System, Metadata.
Skillset gained: Autopsy, FTK Imager, Exiftool, Python, Microsoft Excel, GPXSee.
Learning outcomes: Investigate digital artefacts against a realistic brief, preserving, analysing, and interpreting the evidence. Apply scientific techniques and use scientific terminology appropriately in the context of digital forensic analysis.
Please do read my next blog (Overview of Cyber Security and Management Modules – Part Two) to understand the rest of the modules covered in the Cyber Security and Management MSc course.
It's all about your security and SAFETY!
Follow the simple rules in your life so that you can keep yourself and your data safe and secure:
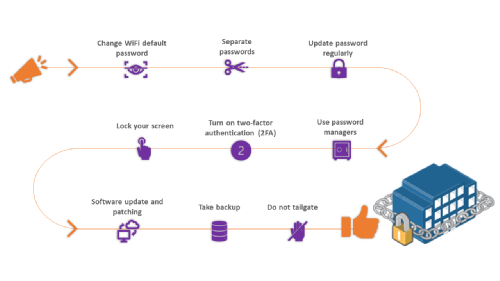
Change default WiFi password – If one has received a default password of WiFi, then they must change the password. This step will protect you in case your default password gets hacked.
Maintain separate passwords for personal and educational (professional) use – The reason being even if your (personal) email gets hacked, your professional email, which might contain sensitive and confidential information will remain protected.
Change your password every 60 to 90 days – It is a good practice updating your password after a defined time interval because it will prevent your account to get hacked as it will introduce the element of difficulties to crack the password.
Use password managers – Do not use standardised keywords as your password as it will be simple to brute force and identify. Create a unique password and store them with the help of password managers.
Turn on two-factor authentication (2FA), where possible – 2FA gives you a provision of sending a code to a second factor that is accessed by you and only you, such as a mobile phone or app. It will make sure your data gets protected with multiple layers of security.
Ensure you inculcate the practice of screen lock for all your smart devices – With the advancement in technology, one could use biometric like a fingerprint or retina lock to enable screen lock, which makes it difficult for an attacker to unlock your smart devices.
Keep your computer and installed software up to date – All your operating systems and software providers send regular patches to mitigate vulnerabilities and fix security issues to safeguard your machine and data. The providers expect the users to regularly check for updates and follow the easy steps.
Acquire the habit of taking back up – Upload the most vital data to an external hard drive or cloud-based storage system such as OneDrive. It will help you access your data if your device gets corrupted or infected by a virus.
Do not tailgate – While accessing the university building, if you happen to notice that someone is tailgating, then validate their badge or report to the staff member as that they can take corrective actions against it. We must understand that physical security is equally essential as digital security.
When university students adopt all the above preventive measures, it will keep the cyber attackers at bay.
Networking and its perks...
The day you decide to attend the open day of university, you have started building your network (unknowingly!). The reason I emphasise building connections is that the people with whom one interacts might help them during the admission process. Based on my personal experience, I communicated and built a professional connection with a resource from the WMG admissions committee team and to date (s)he assists me in stressful academic situations.
I am not asking you to make connections for your benefit and selfish reason. Remember, it is a two-way streak. You build your network to rely on for support, guidance, and help, where possible. It may also reap your big rewards in the long term. At the same time, you must extend your helping hand in their (your connections’) vulnerable time. Irrespective of your designation, you must build your connections to progress ahead as every individual in your network matters.
At WMG, University of Warwick, your connections will begin by working or studying together in groups and being an active team player. Formulating a group is one way of building your network, as everyone in your group will know at least one new student with whom you can get connected. The latter technique expands your group and connections. Alternatively, being a member of societies will expose you to communicate with staff and students at the university.
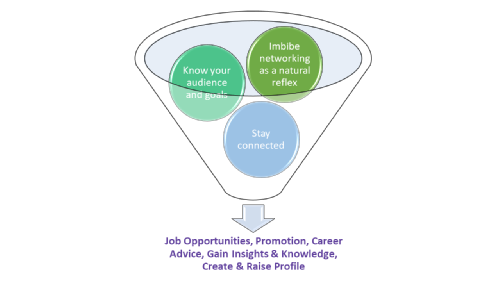
Here are some tips for building your network:
Imbibe networking as a natural reflex – Do not overdo it but if you shy away from people, try to practise it in your daily routine.
Know your audience and goals – Before you attend a social event, aim at how many people you will connect with and what piece of information you are looking for.
Stay connected – Once you have connected with an individual, try and maintain the relationship with them by following up and do not lose your connections and the time you invested.
Remember to continue expanding your network in your professional life by connecting with your clients and colleagues at social events or drinks. It might help you - securing new job opportunities, a promotion at work, receive career advice and advance in your area of expertise, gain insights and knowledge, create and raise your profile and many more.
Let’s get down to the nitty-gritty of modules…
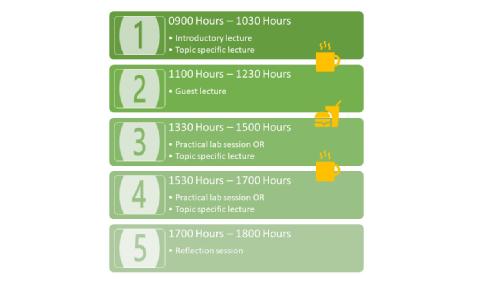
Based on my experience, every module last for five days (usually Monday – Friday and may vary depending on public holidays). All my modules were worth ten credit points; hence, I had to invest one hundred hours for each module and achieve the specific learning outcomes. Now, out of these one hundred hours, I had to attend forty hours of taught sessions. More or less, the days during the module week can be visualised as:
0900 Hours – 1030 Hours: First session of the day.
1030 Hours – 1100 Hours: Break
1100 Hours – 1230 Hours: Second session of the day.
1230 Hours – 1330 Hours: Lunch Break.
1330 Hours – 1500 Hours: Third session of the day.
1500 Hours – 1530 Hours: Break
1530 Hours – 1700 Hours: Fourth and last session of the day.
1700 Hours – 1800 Hours: Reflection session of the day.
NOTE: It depends on the module tutor how (s)he designs the timetable for the week, and your break timings, start time, end time and other things vary accordingly and sometimes changes on the fly based on the speed at which lectures finish.
Day One – First session is the module introduction entailing the topics covered in the module week and a quick walkthrough of the timetable. This session may include an icebreaker introduction of students with module tutors and each other for the first few modules. The second session can be a guest lecturer where an expert on the topics covered in the module will come and share their experience and cite real-world examples where possible. Mostly, during a technical module third, and fourth sessions consist of practical lab work where we explore a tool and try and implement our theoretical knowledge learnt during the first two sessions of the day. If it is a non-technical module, the module tutor will cover specific topics in the third and fourth sessions.
Day Two and Day Three – Both these days, follow the same trend as day one, except for the fact that the first introductory session is replaced with a topic-specific session.
Day Four – In a given scenario, if your grades comprise IMA plus PMA, then the mini-case study question is announced, and you either need to work in a group or individuals and present your work on the following day. However, if this module is graded purely based on PMA, this day will be the same as day two or three.
Day Five – It is a big day as you got three significant tasks: present your IMA work which consumes two sessions; receive, discuss, and understand your PMA question consumes the third session of the day; and finally, reflection and feedback that calls for the last session of the day and week.
You have earned your weekend! You need to relax, but please do not forget to start working on your PMA from the following Monday as the module is fresh in your mind, and you can get the most of it done in the following week without breaking your chain of thoughts.
Module Assessment - Behind the scenes!
An innovative learning pathway of studying Post-Graduate Taught courses at WMG, University of Warwick is to get assessed based on deliverables submitted and not dependent on written or oral tests or exams. We shall understand different types of assessment. Furthermore, different types of scenarios we should expect and, most importantly, what skills should we possess and which of these skills will get enhanced in our journey. Food for thought: To understand at the beginning of the module how will the module be assessed.
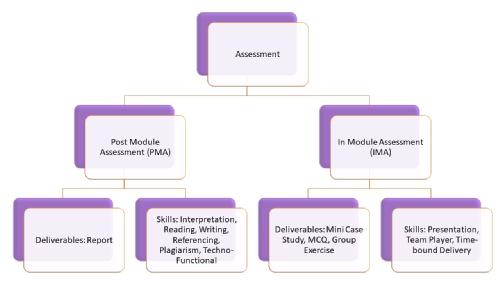
Types of assessment
Post Module Assessment (aka PMA) – As the name suggests, this type of assessment takes place after the module delivery week.
What to expect? The essence of PMA is to deliver a report based on a case study. In my case, we (the students) were supposed to be the cybersecurity specialists/professionals working in a cyber security firm and analyse the current framework, estimate, and recommend future security architecture for our clients. Please make a mental note that these clients can belong to different sectors like finance, healthcare, utilities, and many more.
Which skills get enhanced?
Interpretation – Understand the background of the case study and the question that needs to be addressed. The key factor is to understand your audience for whom is the report targeted.
Reading – Improve your comprehending skills and inculcate speed reading by studying as many articles related to the topic and pick the best ones based on your critiquing practice.
Writing – Adhering to word count, presentation in terms of the page number, header, footer, uniformed font style and size, dedicated heading and introduction and conclusion to each section.
Referencing and Plagiarism – Follow your department referencing style and all the protocols of plagiarism. Ensure you complete both the training available on Moodle.
Techno-Functional – Think like a professional technical employee possessing functional knowledge of the domain.
In Module Assessment (aka IMA) – This type of assessment happens during the module delivery week.
What to expect? Solve a mini case study, answer multiple-choice questions, group exercise or others. For instance, we have been provided with a data file to perform geospatial analyses, formulate a brief presentation, and deliver the group presentation.
Which skills get enhanced?
Presentation – Creating slides, posters, excel data and stitching the group work and verbally present the group work.
Team Player – Distributing tasks among students in the group, and then collaborating their ideas and work into a single deliverable.
Time-bound Delivery – The group tasks are designed to be completed within a dedicated timeframe and present to the board with a constraint of time.
If you note carefully, all the skills are interlinked, and you should not try and master only a particular skill or develop a specific skill-set.
Day One, Induction Week, First Semester - What to expect?
I vividly remember 05 October 2020 (Monday) was my first day at WMG, University of Warwick. I started my Cyber Security and Management course, after nine years of work experience, with nervousness and excitement since student life (again!) and UK University and study pattern were new to me. I echo you all in terms of cultural difference is different in case you are an international student. Apart from the lift and shift in lifestyle, I worried about what I need to do on my Day One and the following weeks and first semester?
Please keep reading, and I will narrate my experience, but unfortunately, I cannot promise you that we will share the same journey.
Before the induction week, I got a timetable for the week wherein I had to book my sessions on an internal port called myadvantage. These planned week-one sessions focused on course introduction, module list – mandatory and elective, types of module assessment, pre-requisites of technical sessions, and other social events like meeting your cohort. Irrespective of the virtual world, these sessions were planned as face-to-face and running online for virtual students.
Moving ahead in the following weeks, I was expected to complete training covering the significant aspect of plagiarism and referencing assignments. First, I had to assimilate the Harvard referencing style, followed by the University of Warwick and my department. Our course leader recommended few tools such as MindManager, Endnote, LaTex, Visio, InkJet to install and do self-learning as it will help us during our assignments.
Additionally, this period is the best time to tailor your CV and apply for graduate scheme roles. Exploit the careers team at the University of Warwick, schedule one-on-one sessions with them, and prepare yourself for the interviews. Participate in more such activities and attend seminars or talks organised by the companies that are relevant to your course and future.
Soon, I got my timetable for the entire year, excluding the elective module as the portal to choose our optional module opened by the end of November. As I had a breathing period to decide my elective modules, I scheduled a meeting with my course leader and personal tutor to understand the best suitable modules based on my background, experience, interest, and future growth.
Watch out for the space for project selection as the process started for me at the beginning of November. You will be expected to apply for different projects and attend a brief formal meeting with your future supervisor. Please ensure that you finalise your project topic and supervisor by the end of November. I managed to secure my dissertation within one week (Shhh!).
I did attend modules during my first semester, which I will be writing more in my next blog on module assessments and what happens during the modules.
We accept and support YOU!
Happy Pride Month!
The University of Warwick's core purposes, namely, Research and Education, will advance and become stronger by four key strategic priorities. Inclusion is one of the priorities that enable us to gather talented and skilled students and staff from across the globe to be part of the university. Our diversity and inclusion priority aims to remove the social, economic, and cultural barriers by providing equal opportunities to everyone irrespective of their background, race, faith, gender, disability, and sexual orientation.
At WMG, University of Warwick, we firmly believe that people who define themselves as LGBTQUA+ could choose to share sexual preference or gender with their classmates, teachers, or anyone. We respect your decision if you wish to remain discreet and do not want others to be aware of your sexuality or gender. Coming from a developing country like India, I sympathise with individuals bullied by other undergraduate students, their family members, or society. I promise you WMG, University of Warwick is a safe place to be, and you will be accepted if you decide to be yourself! However, I am sure time is changing, and every country is trying its best to evolve itself in terms of inclusion and diversity.
How different are we?
We have set four themes that form social equality/inclusion equality objectives for 2020 – 2024. In a nutshell, these themes target to increase diversity, imbibe the diverse culture, and create an inclusive environment on campus to become an internationally recognised leader in education.
Formulated Rainbow Taskforce to help in the progression of LGBTQUA+ equality at the university. The advisory body makes recommendations to the social inclusion committee to represent and raise awareness of LGBTQUA+ matters and positively change them.
Lastly, you would see pride events being organised and promoted on the official websites such as the myadvantage Warwick website. Online events have an option to log in as an anonymous user if you wish to remain discreet.
We hope to sow the equality, inclusion, and diversity seed so that the professional world can reap the fruit of respect for sexuality, ethnicity, gender of other individuals. Maybe a few years down the line, we hope to celebrate each day as Pride Day and not wait for half of a year to end and celebrate Pride Month in June.
Teams is my new companion.
Somewhere in the world, one of the students must have dreamt of attending lectures from home in his/her comfy clothes. Now, we all would agree that dreams do come true! (Food for thought: Keep Dreaming and Carry On Reading).
What a year it has been! In the new-normal virtual world, we (the students) were meant to attend the university remotely and expected to grasp the knowledge shared via our computer screen. To bridge the gap between tutors and students, we need an interactive tool, and Microsoft introduced an application called MS Teams to integrate technology and humans.
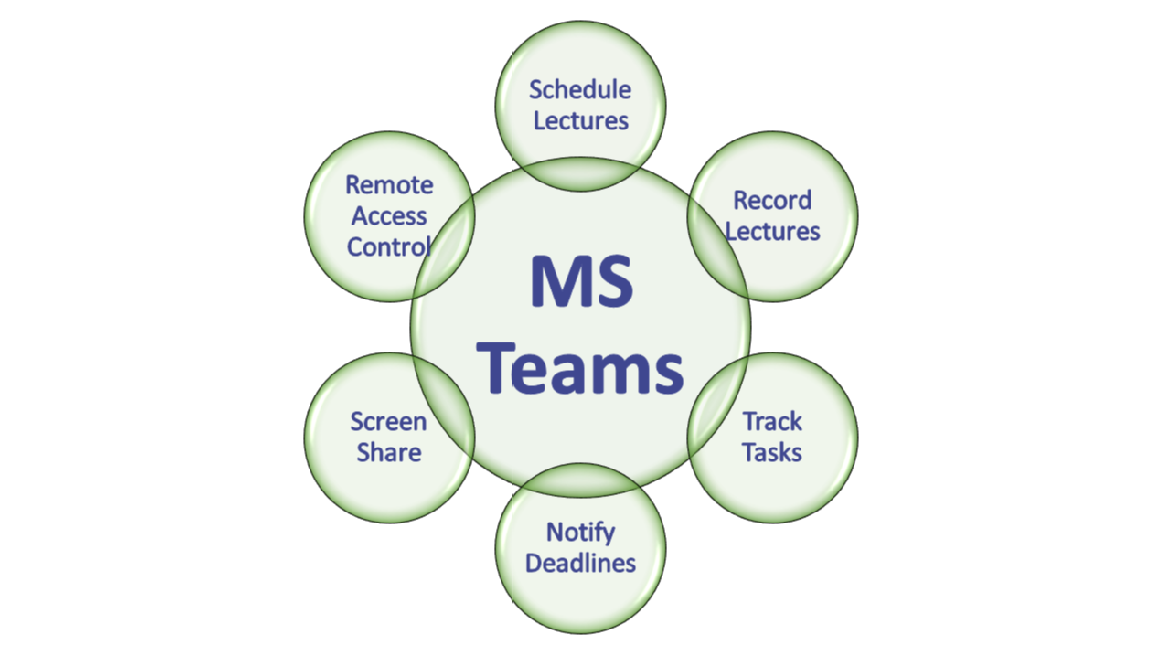
What features does MS Teams provide?
- MS Teams allow you to set up lecture sessions for a maximum of 250 students (as we speak).
- Create mini-groups/teams and add students/friends to your study groups.
- Upload class materials under the “Files” tab in the teams created. At the same time, you got the power to control access such as read-only or read and edit, etc.
- Record meetings - If everyone active in the session has given their consent, you should record the meeting. It is also possible to download or view the recording online later while you revise the module or work on your assignments.
- Setup tasks, internal deadlines, and notification – You can assign tasks to different team members and collate their status. Parallelly, an email notification could be scheduled so that your teammates all mindful of the time left for our deadline.
- Create, Save, Modify Files – You or your entire group can work on files together within MS Teams without opening them in your respective application.
- Share your screen – You can present your entire computer or specific screen, including playing a video along with its audio.
- Control screen remotely – When you need technical assistance from your tutor or IT technical analyst to resolve any specific error faced during a module.
Teams Lecture Room Etiquette
- Keep yourself Muted unless told or wish to speak.
- Raise your hand if you have a question.
- Share your thoughts or questions via the Chat tab.
Sometimes, my morning tea begins with an MS Teams meeting, whereas few days end with late-night study with my classmates. That is why I say Teams is my new companion, as it is the only constant in my life during this lockdown blues! My bedroom has turned into a personal library wherein I can sit next to my classmates (virtually and without two meters distance) and start making study notes or have a social drinks session along with fun virtual games.
Lastly, the lecturers love saying, “Please remember to register.” as we need to submit our attendance on MS Teams. Personally, I love this feature as it reduces human dependency!
Dinesh, CSM
Cyber Security ? Or Management ? Why not Cyber Security and Management ???
Ron Weasley was able to re-enter the Chambers of Secrets only after learning parseltongue (language) from Harry Potter (Nerd Alert: Harry Potter Saga). Likewise, you and I need to speak management lingo with a flavour of cyber security to unlock our future secret doors. Now, ask me how is it possible? I would suggest getting you enrolled on the WMG Cyber Security and Management (CSM) post-graduate taught course.
The CSM course strikes the perfect balance between the two profiles, namely, cyber security and management!!!
What does cyber security mean?
Before joining this course, my definition was to safeguard the organisation systems connected with the internet. Because common sense says that we need to protect our computer from virus, and the virus enters our system from the internet. Boy, I was wrong!
We are responsible for defining the security boundaries and protocols of the entire organisation, for instance, physical security (CCTV, etc.). The security ranges from digital files to confidential documents printed such as contracts, design documents, and many more. We look after the three main pillars of an organisation CIA triad known as Confidentiality, Integrity, and Availability to ensure there is minimal or no disturbance to the operational business of a company.
How does management profile factor into?
Enough said about security definition and its roles and responsibilities. You must be pondering where does the management profile fit into these shenanigans of cyber security expertise. We would gain profound knowledge to identify the security gaps in an organisation and then recommend our subject matter expertise. The organisation modus operandi should not get impacted, and we could ensure by designing, developing, and delivering a defence-in-depth mechanism. The entire exercise from inception to delivery of security policies to the client needs an explanation to the C-level executives.
The focus is to translate the advantages of cyber security into monetary gains supported with other benefits to the organisation. In this course, we understand and learn the expectation of the senior management and what they expect in such business reports by identifying the process gap. What should be the unique selling point (USP) so that the client chooses you/your consultancy firm and disregard the other vendors in competition?
To highlight an important factor about the CSM course is that it is open for aspiring students from various other fields and not restricted to technical people from across the globe.
Follow my path, and you shall write your success story soon.
PS: I decided to join the WMG CSM master’s course after being interviewed by the course leader (Dr Harjinder Singh Lallie) as he answered all my questions and welcomed me to the WMG family with open arms.
Dinesh, CSM



